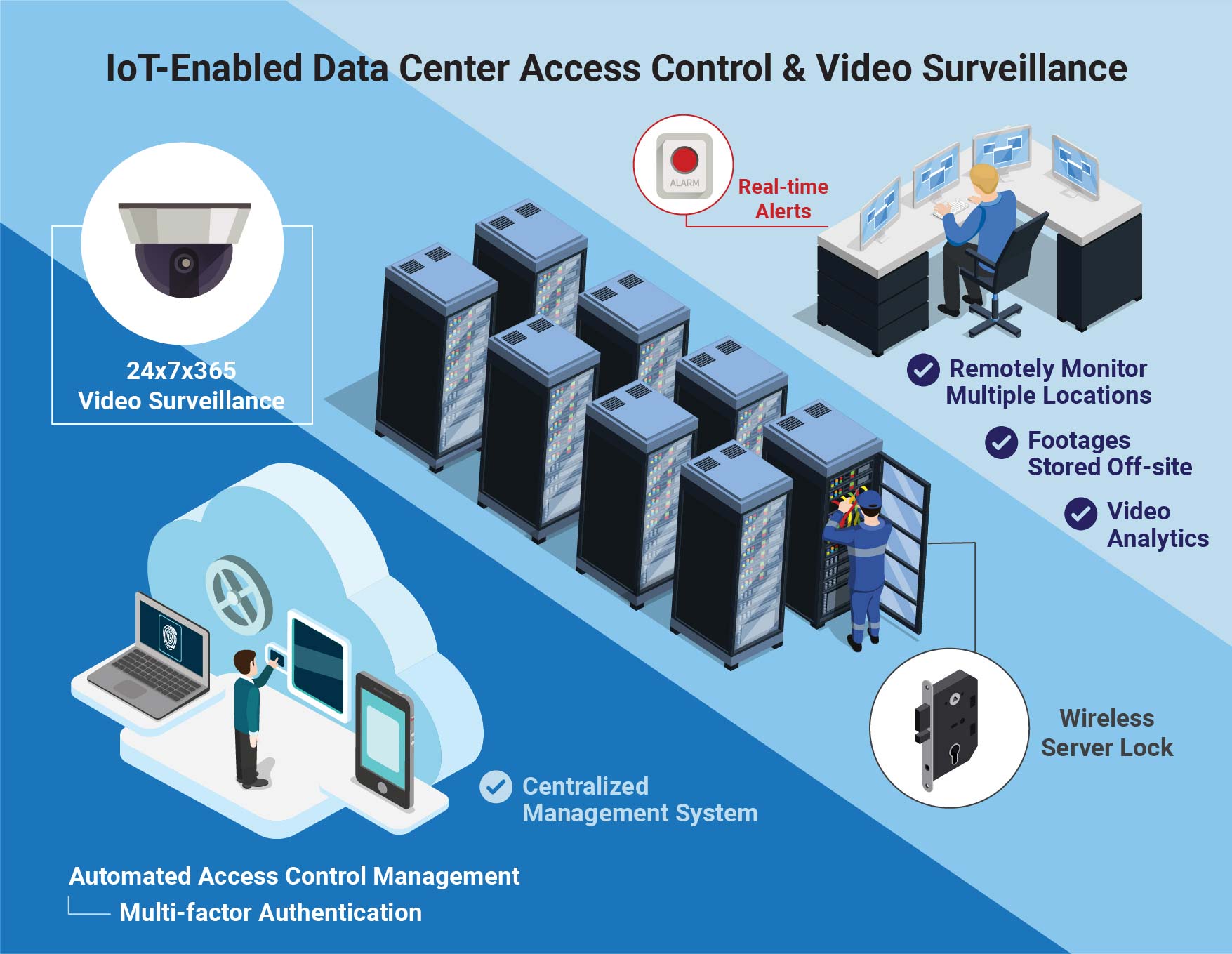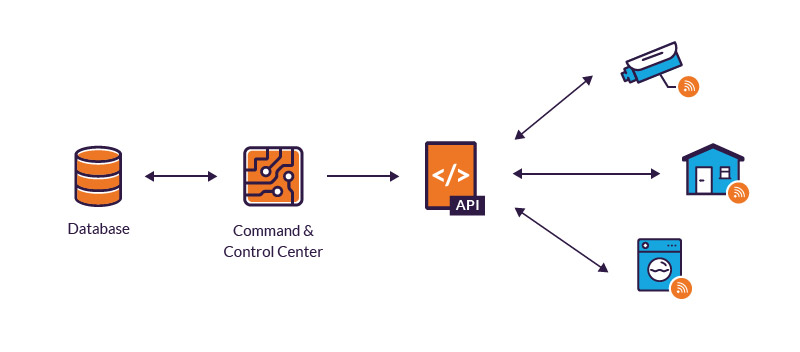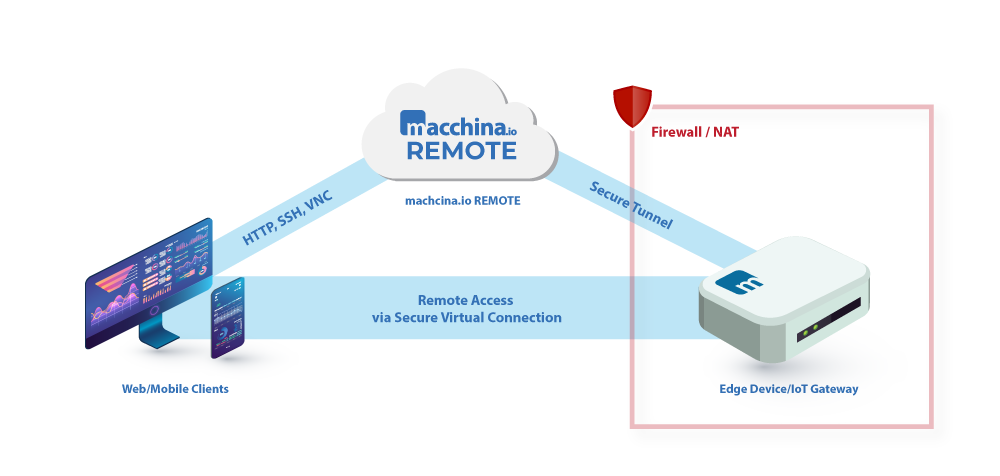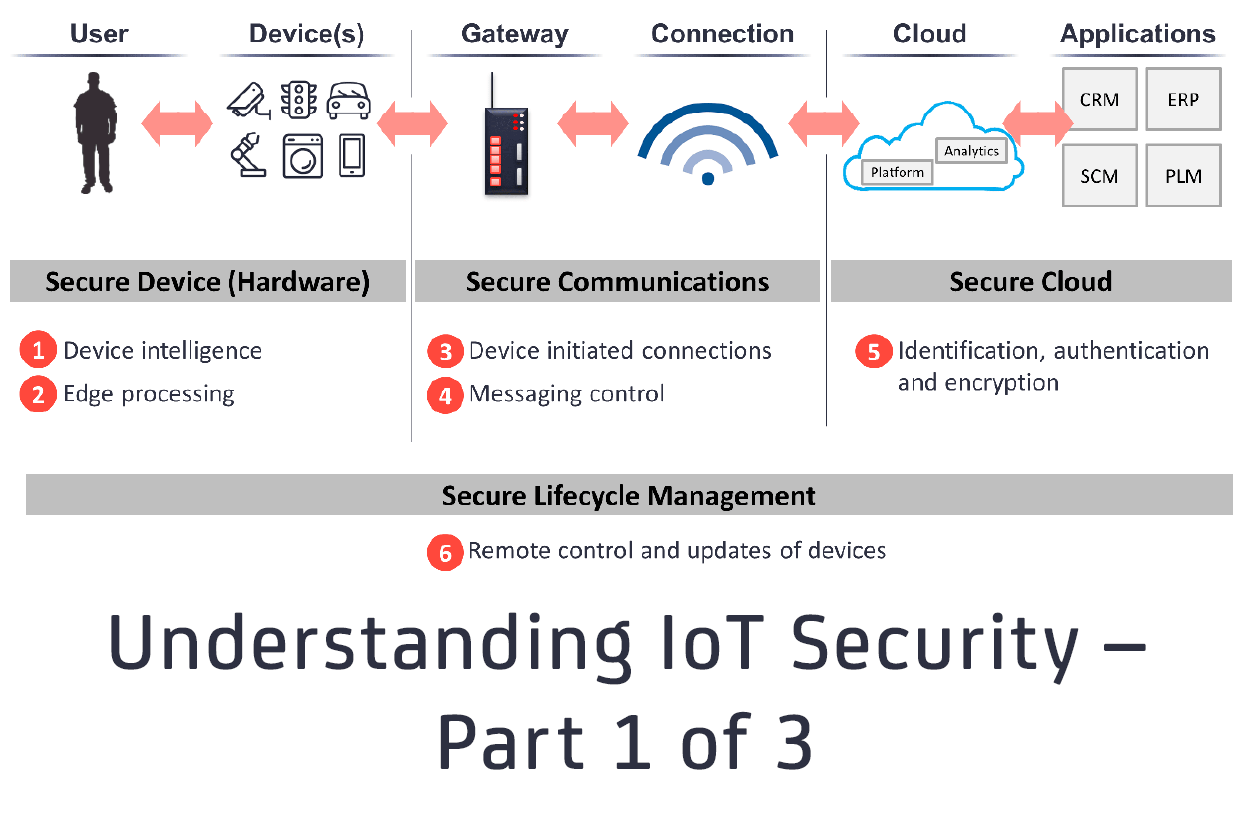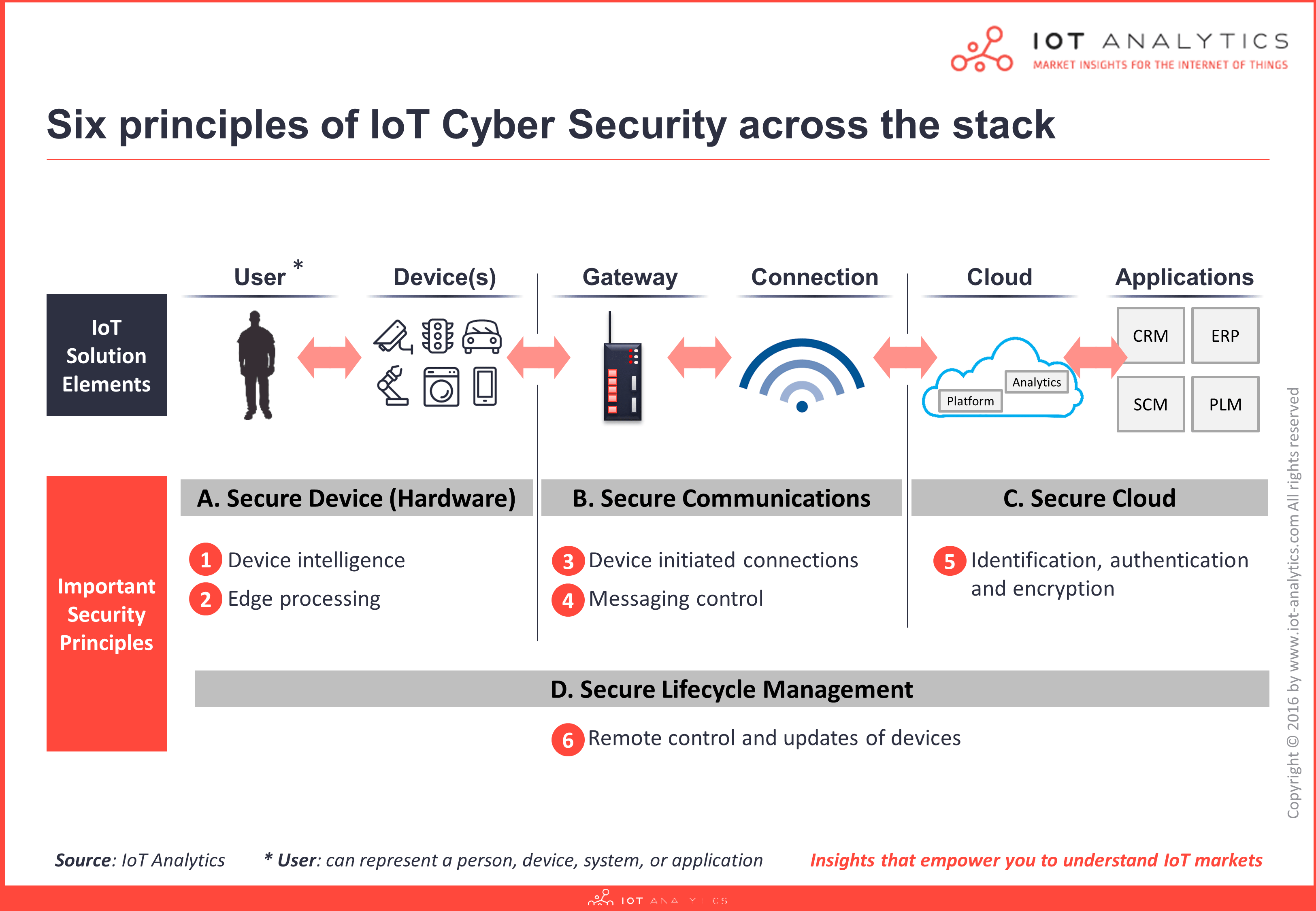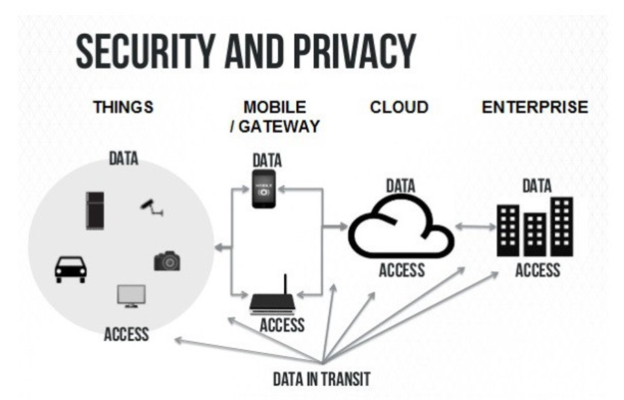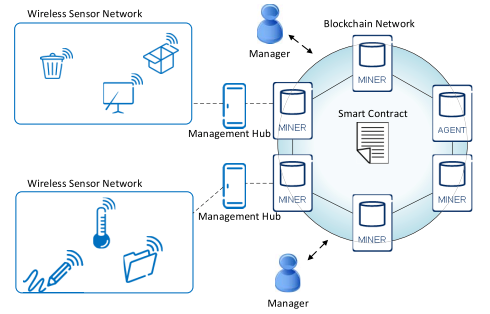
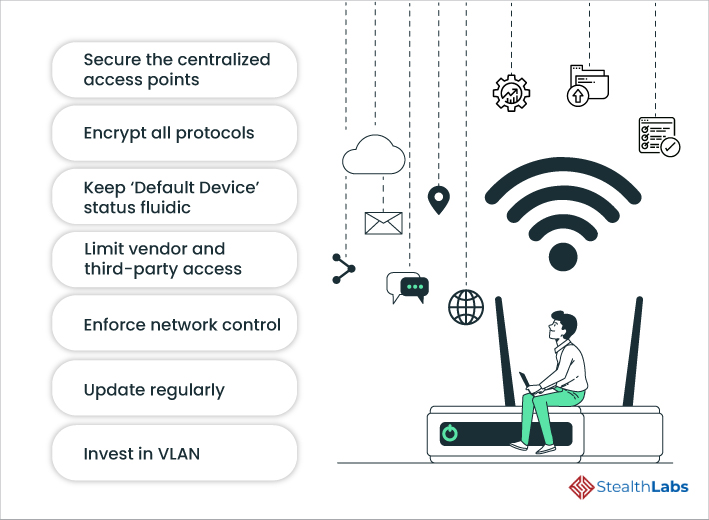
Your must-have IoT security checklist: ENISA's online tool for IoT and Smart Infrastructures Security — ENISA
IoT Security: How to Secure Your IoT Devices and Network - IoT Cloud Platform - IoT Connectivity Services and Consulting - SeeControl
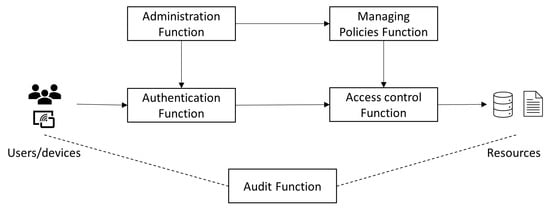
Sensors | Free Full-Text | Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions
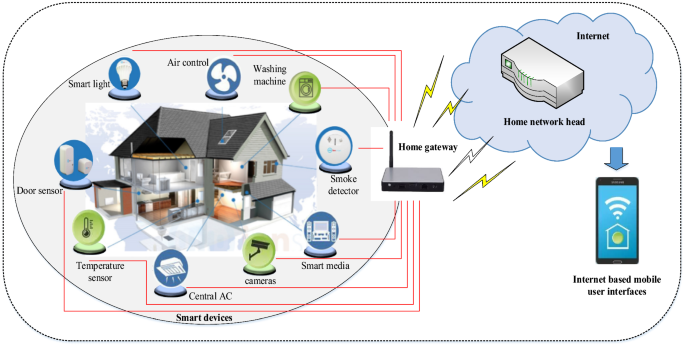



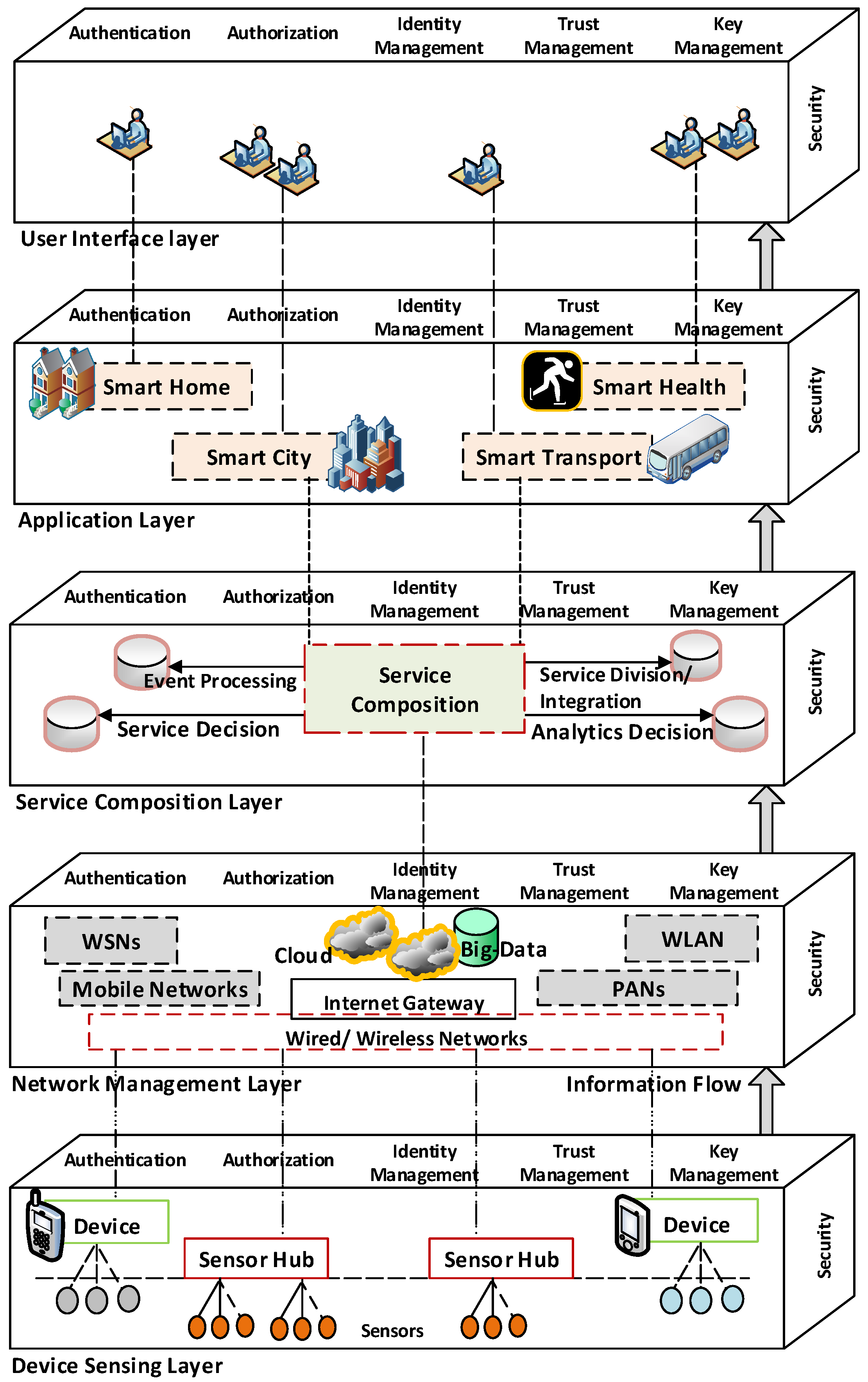
![PDF] Security , Privacy & Trust in Internet of Things : the road ahead | Semantic Scholar PDF] Security , Privacy & Trust in Internet of Things : the road ahead | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a7883e5848fde68041dc150d0d36641d921b8ee9/3-Figure1-1.png)