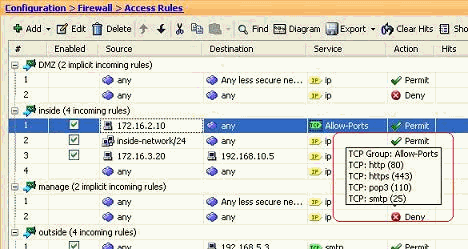
Firewall at best price in Mumbai by Trustly Technology Solutions Private Limited | ID: 2851778085133
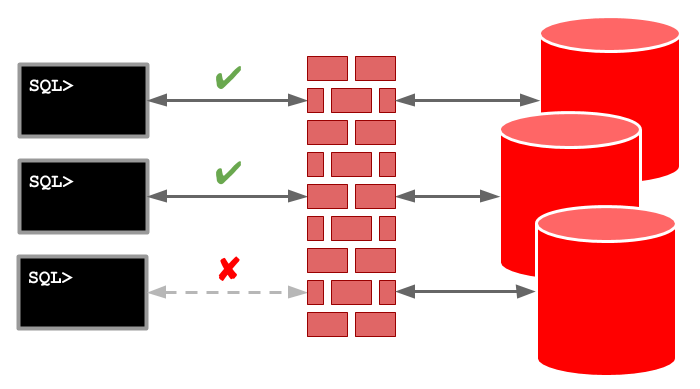
ORACLE-BASE - Service-Level Access Control Lists (ACLs) - Database Service Firewall in Oracle Database 12c Release 2 (12.2)
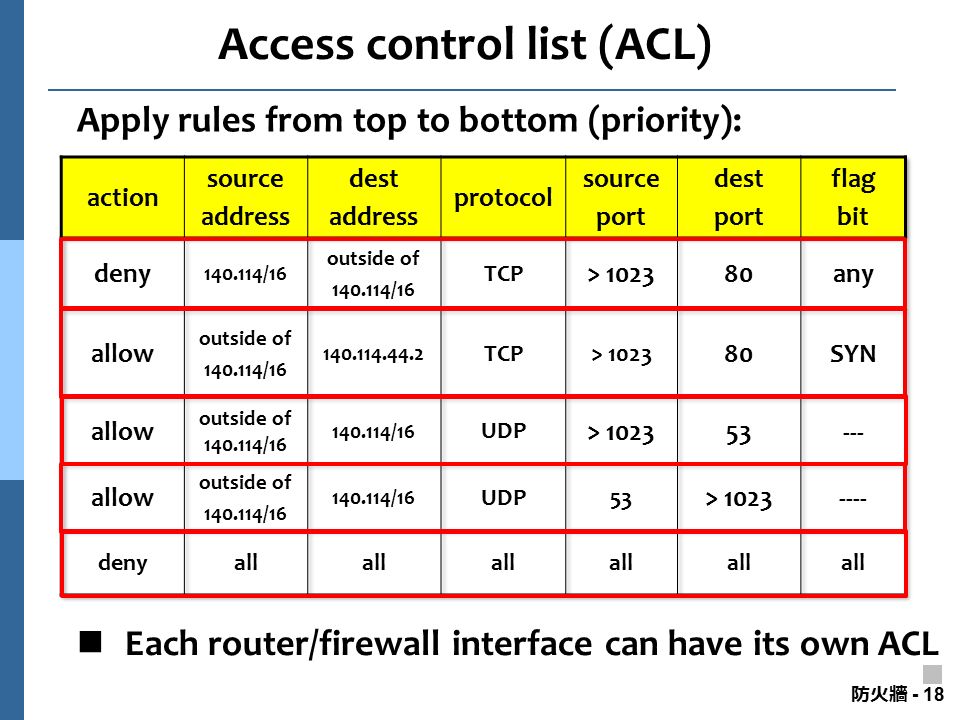
防火牆 Firewall All rights reserved. No part of this publication and file may be reproduced, stored in a retrieval system, or transmitted in any form or. - ppt download

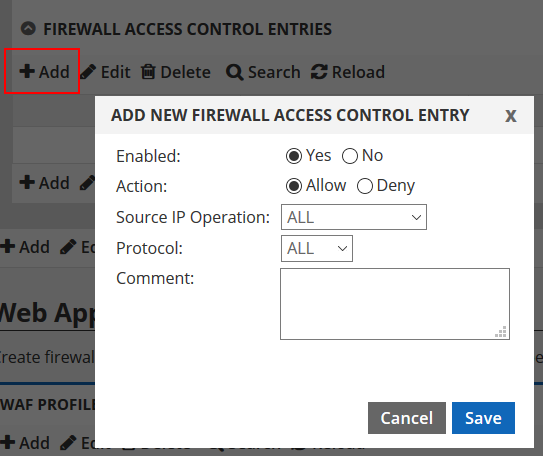

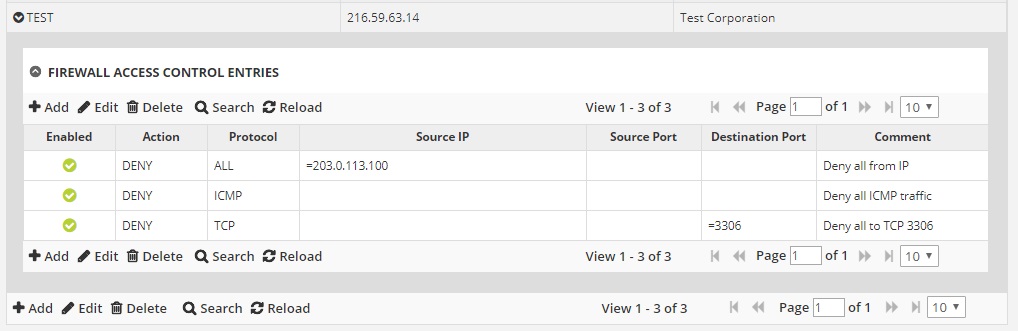

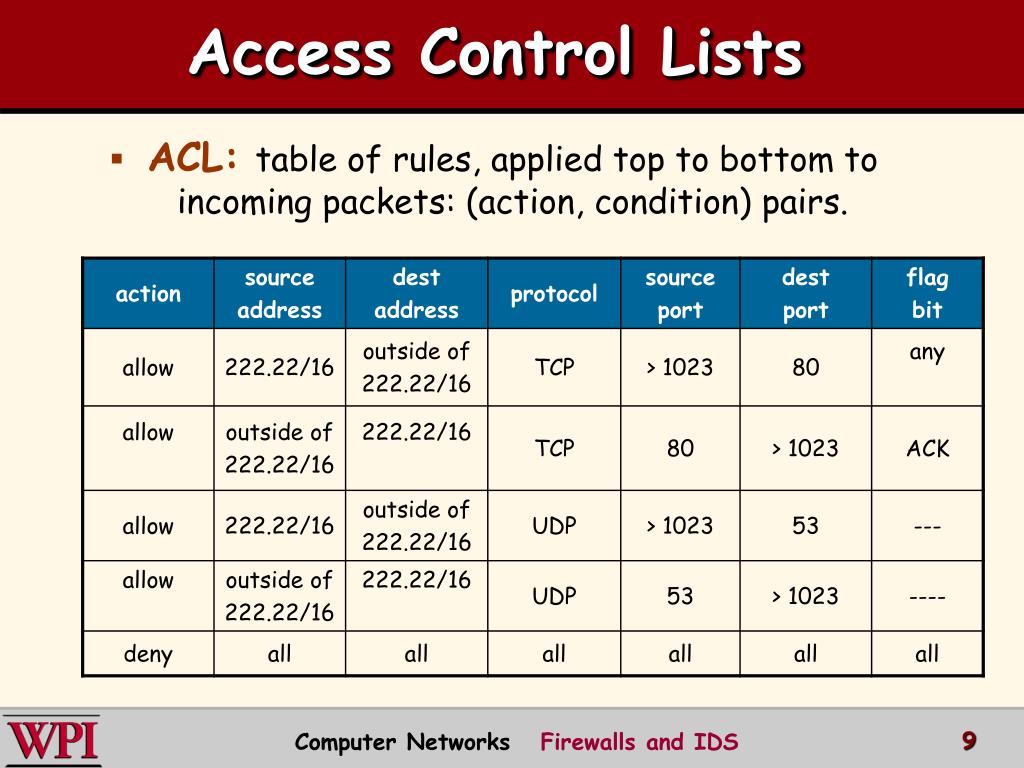

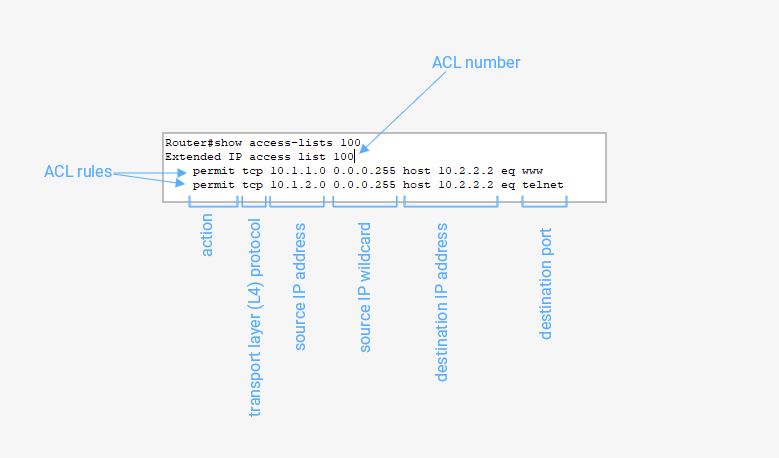

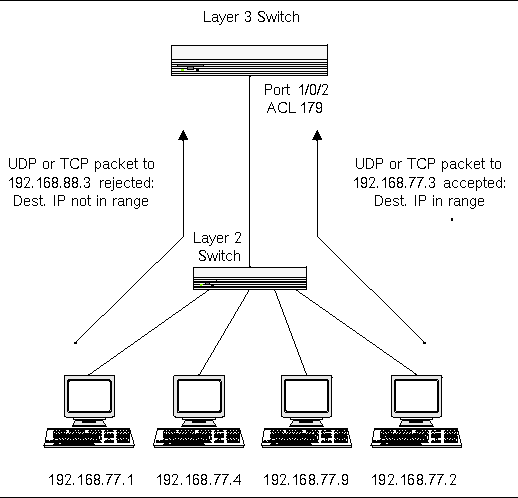
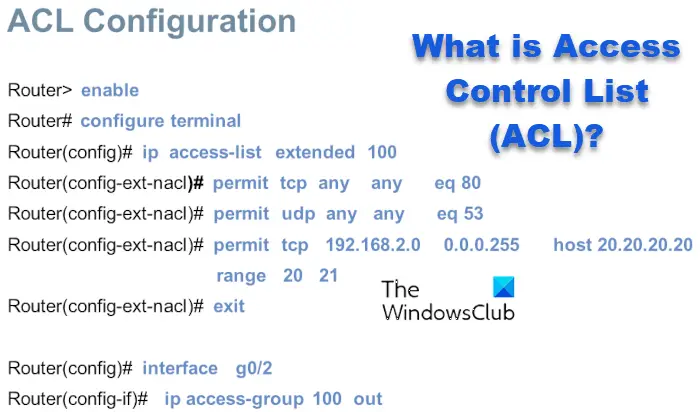
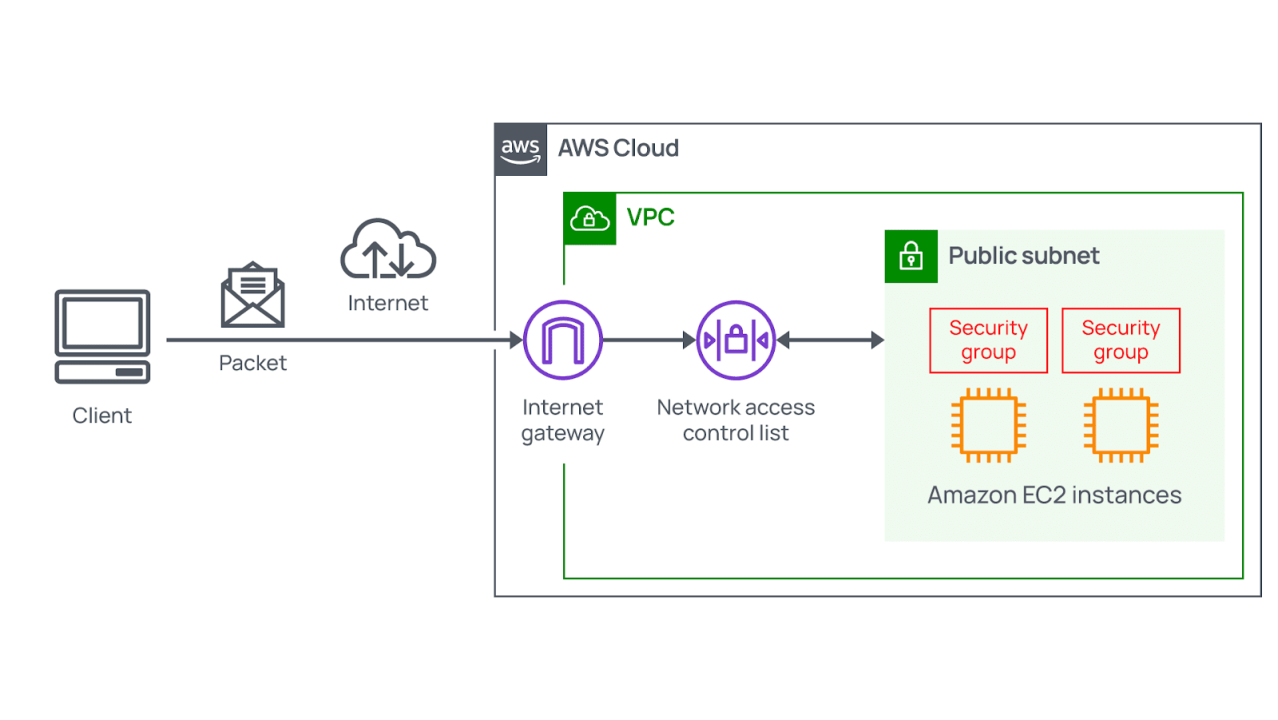



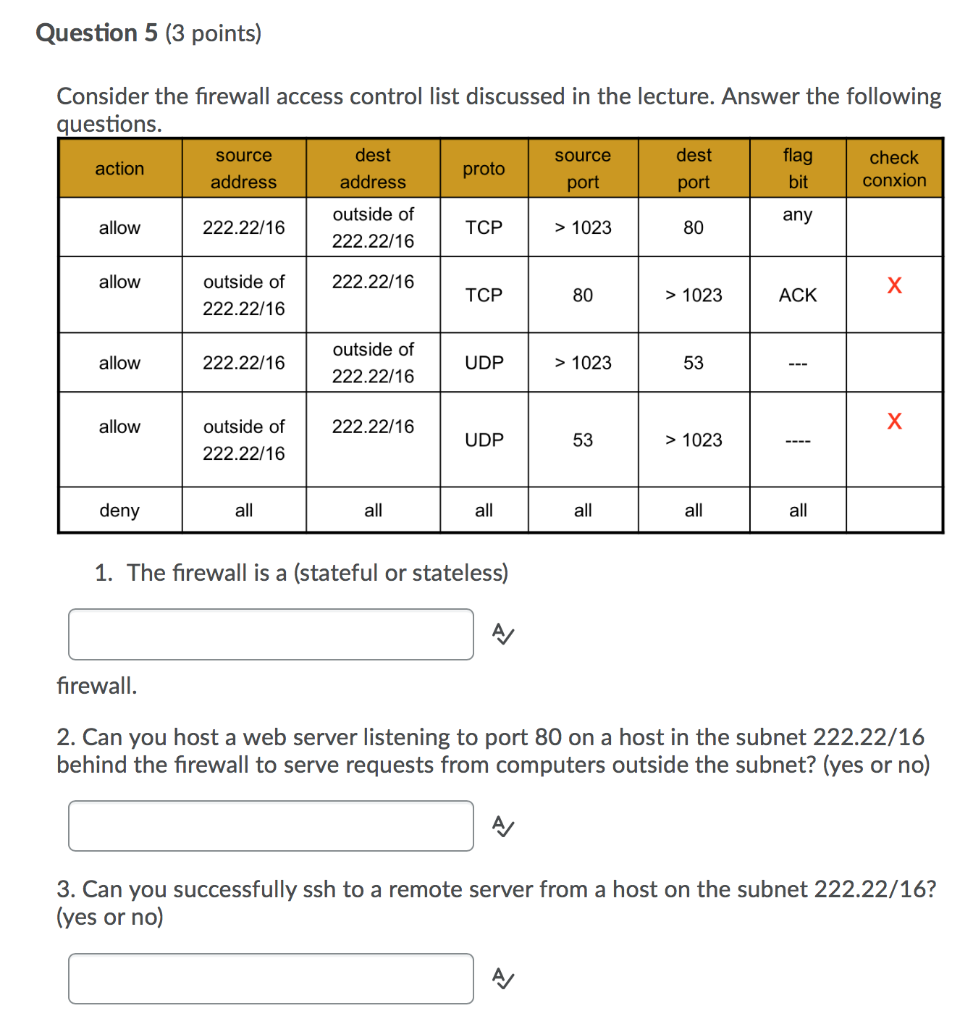
![Access Control List In Networking | bytecode Security [Updated 2024] - Access Control List In Networking | bytecode Security [Updated 2024] -](https://www.bytecode.in/wp-content/uploads/2021/04/Access-Control-lists-Cisco-ACL.jpg)