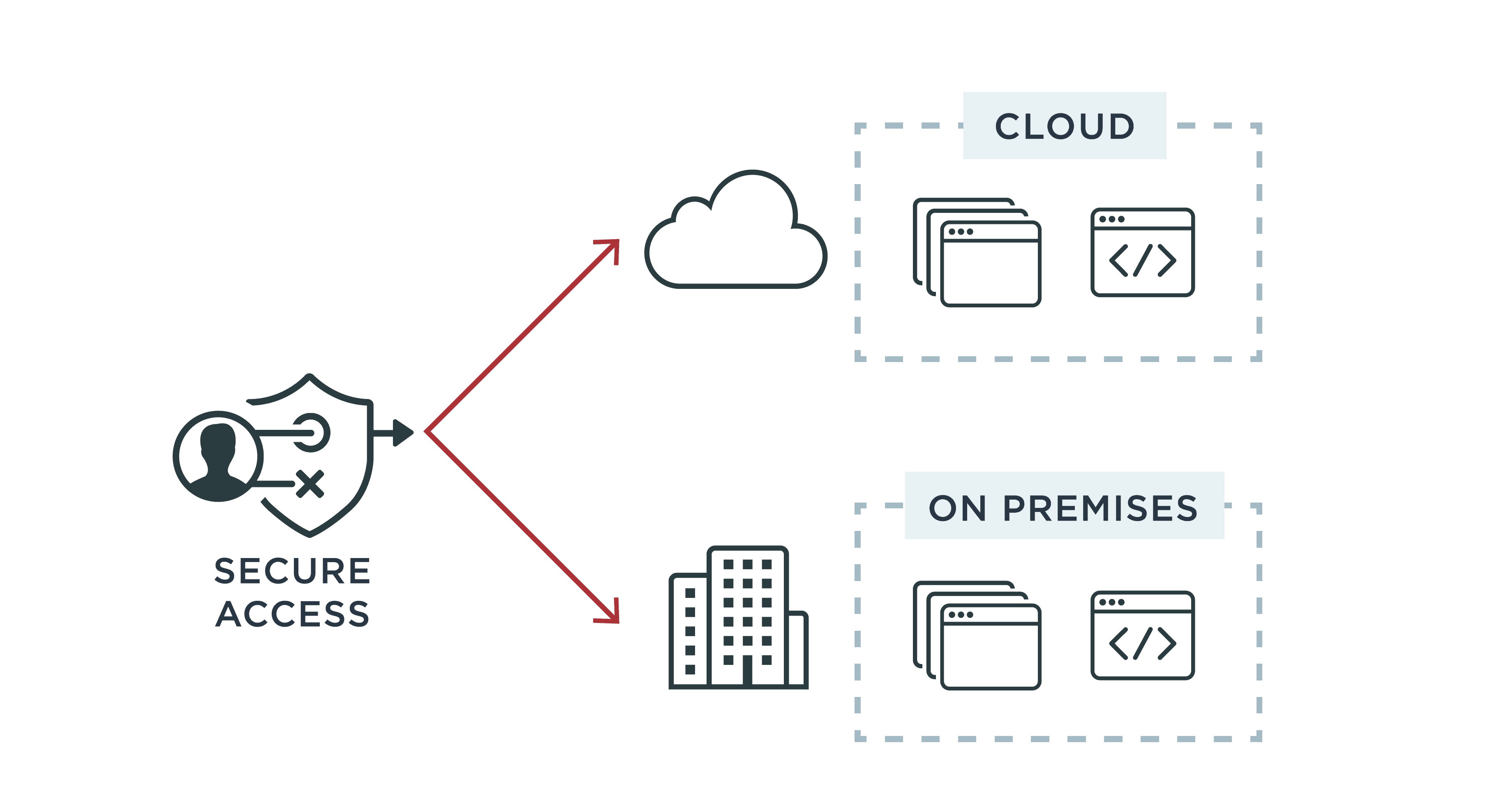
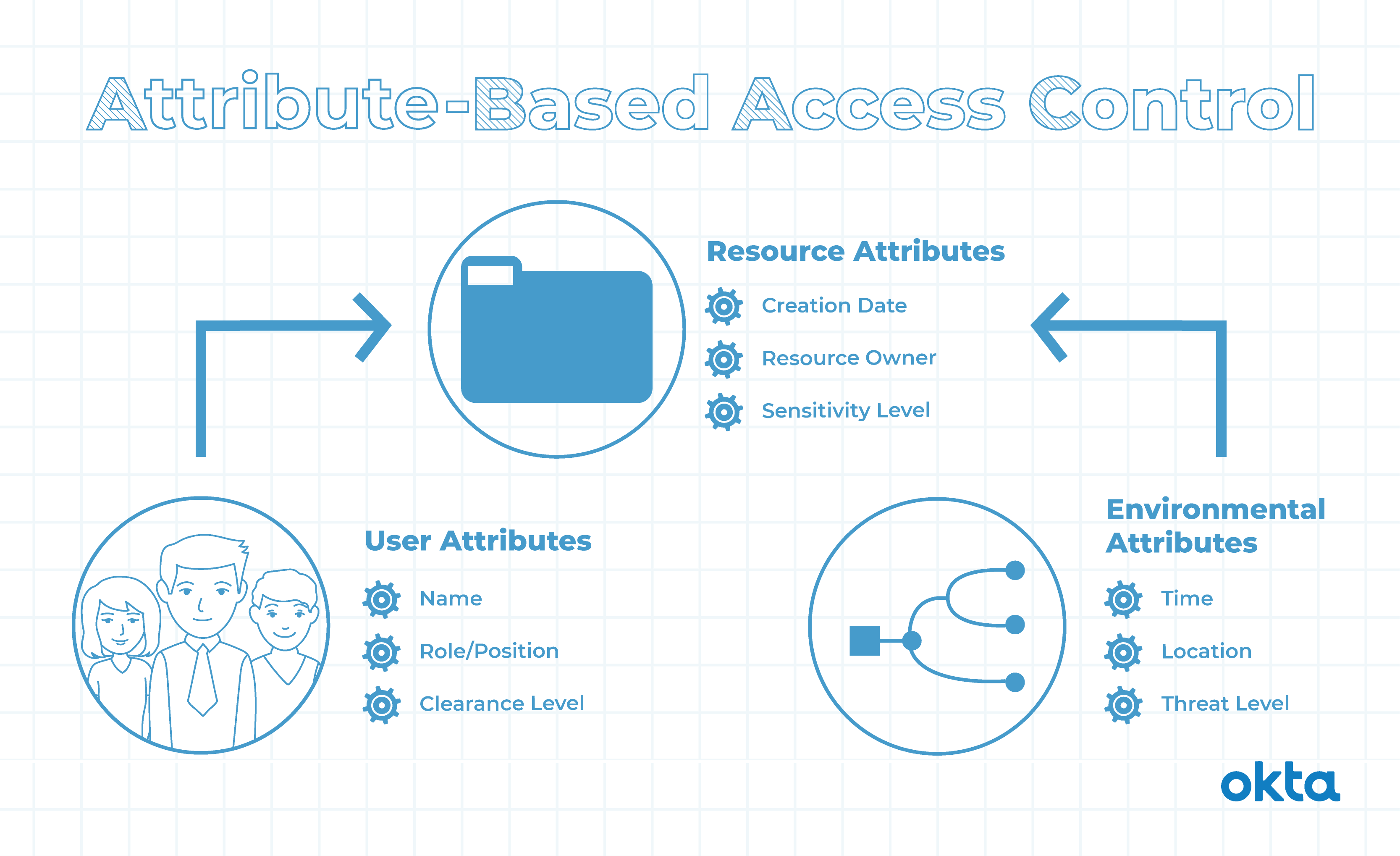
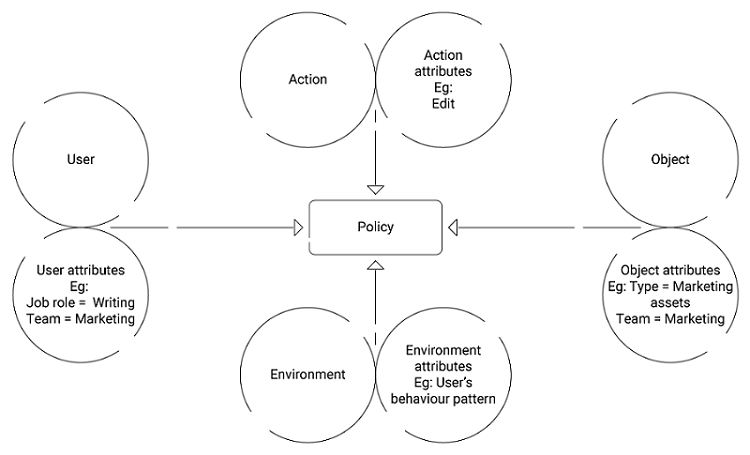
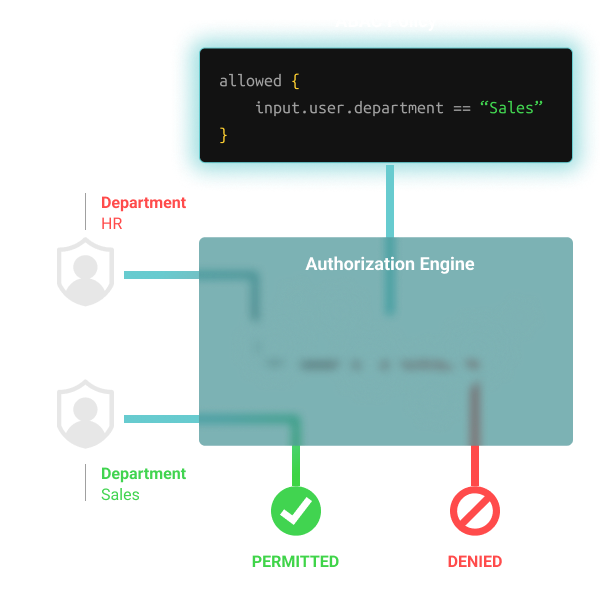
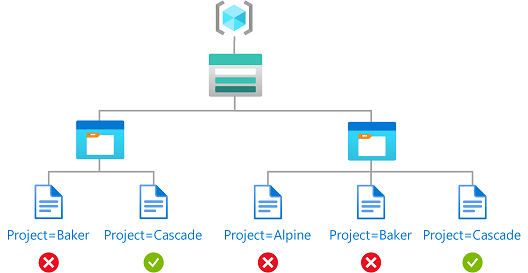
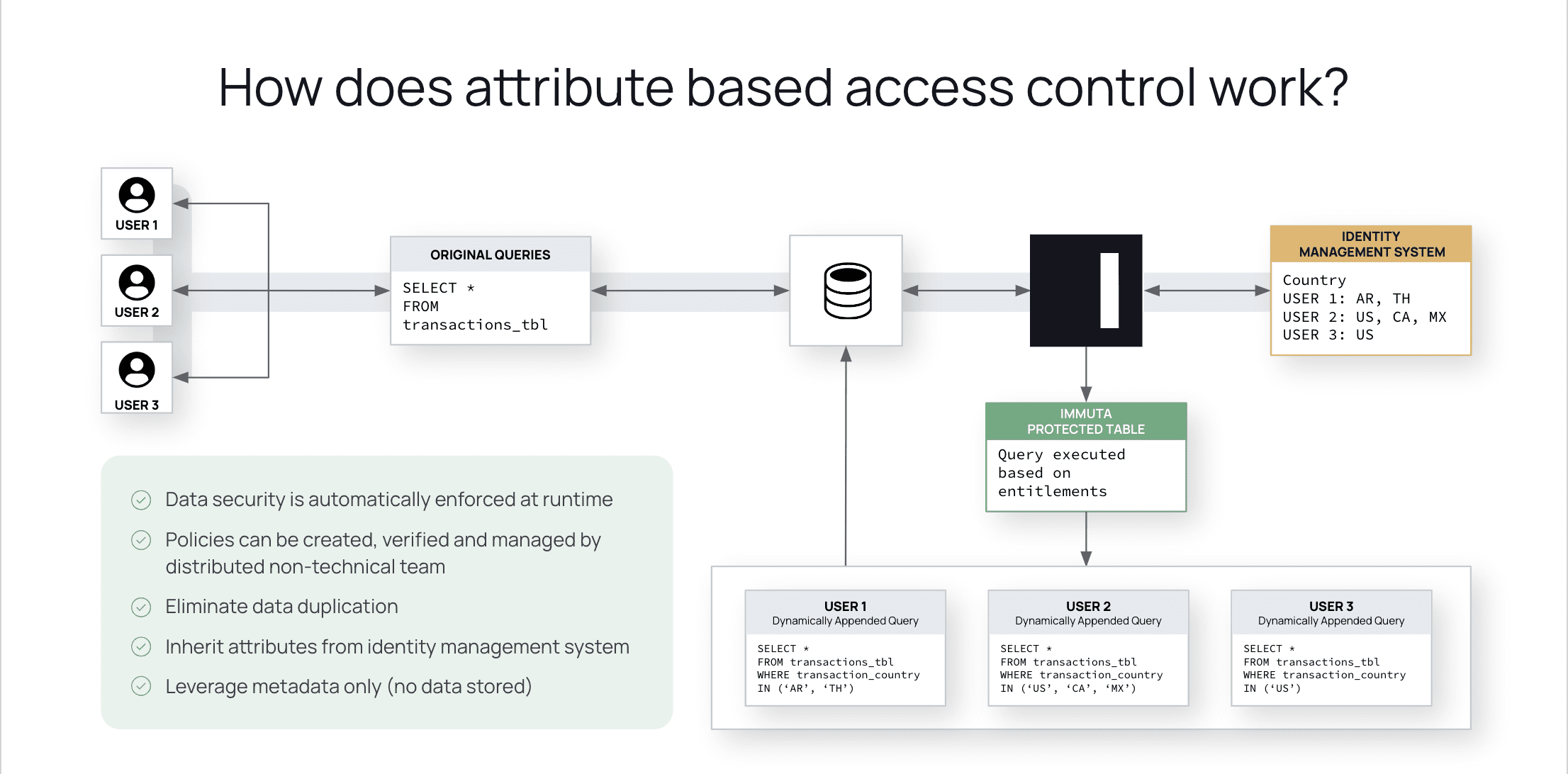
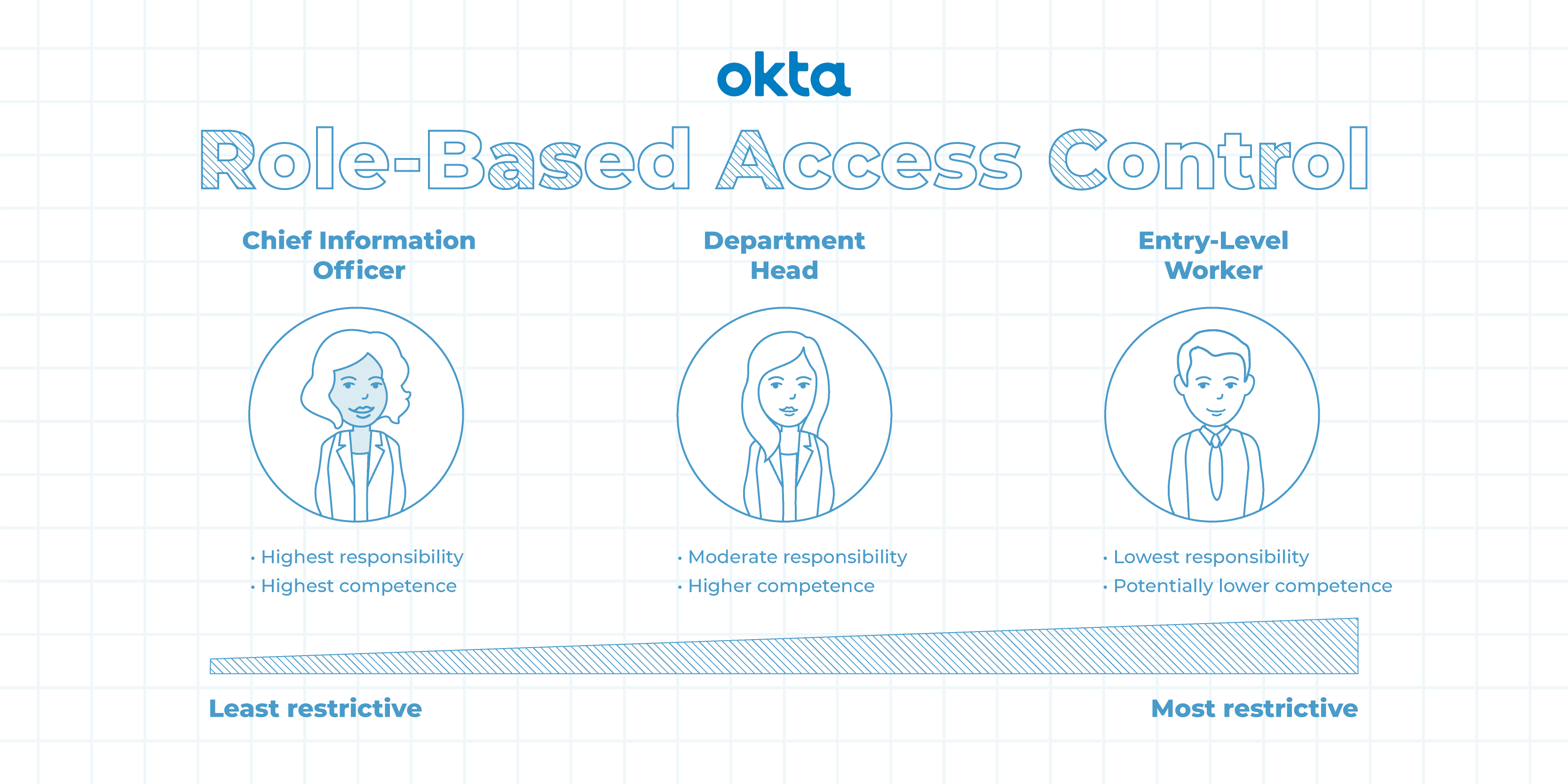
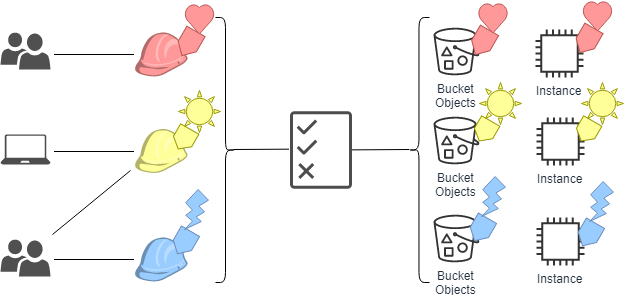
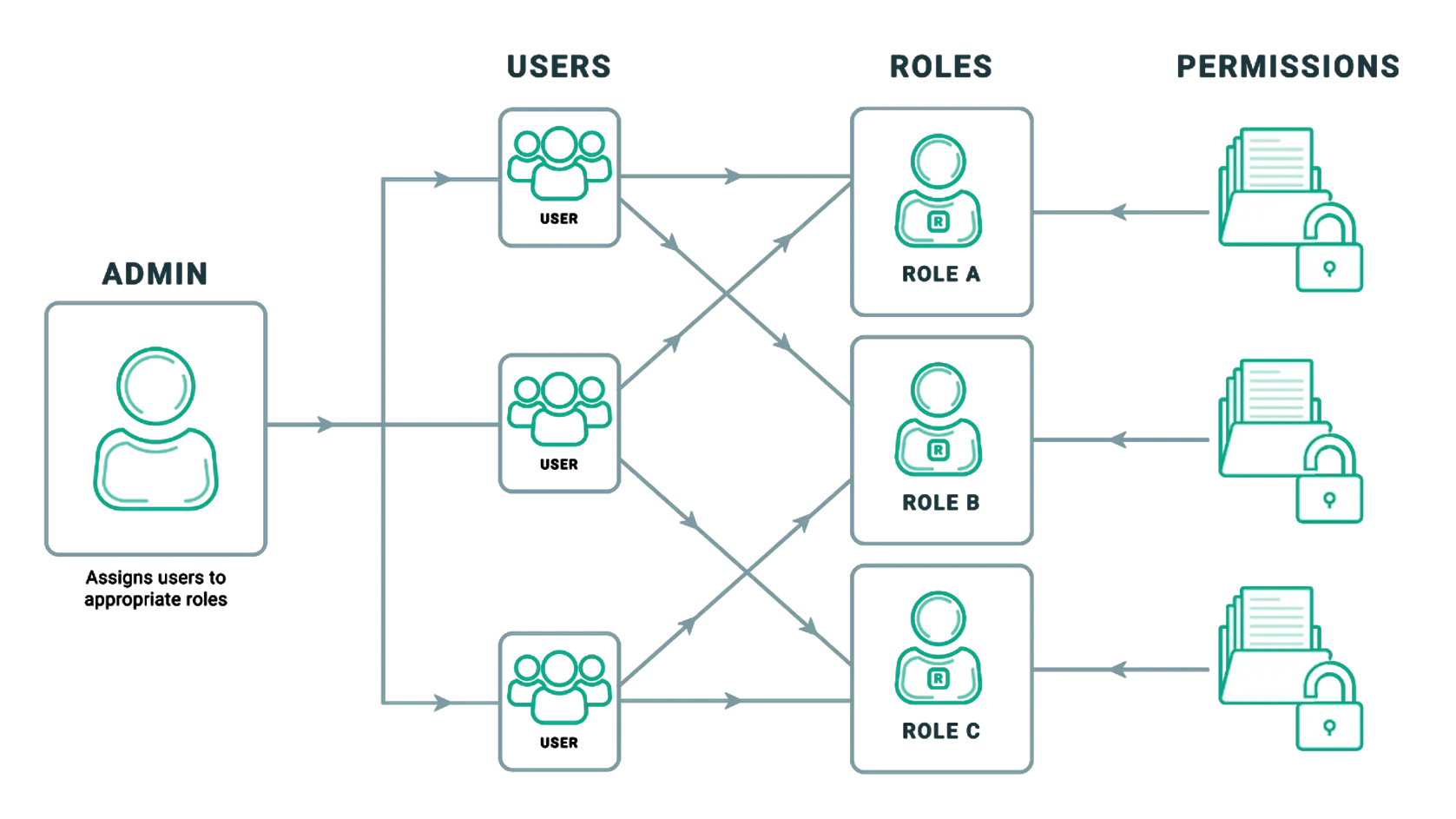
permissions - What is a suggested roadmap towards implementation of a simple Attribute-based access control (ABAC)? - Software Engineering Stack Exchange
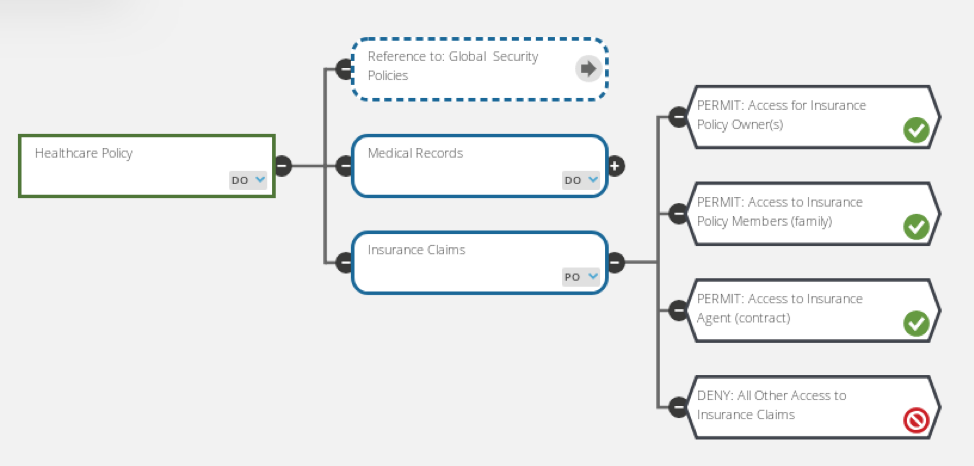
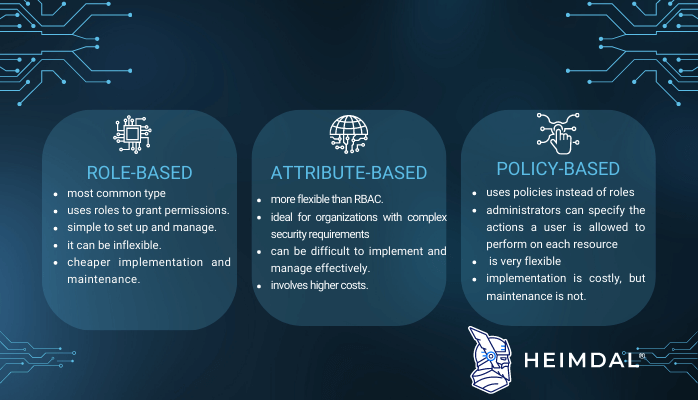
DZone: Why Attribute-Based Access Control - The Evolution from RBAC to ABAC in Data Access Control - Axiomatics
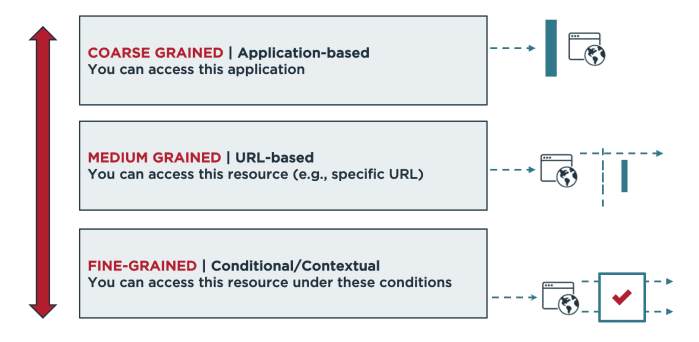
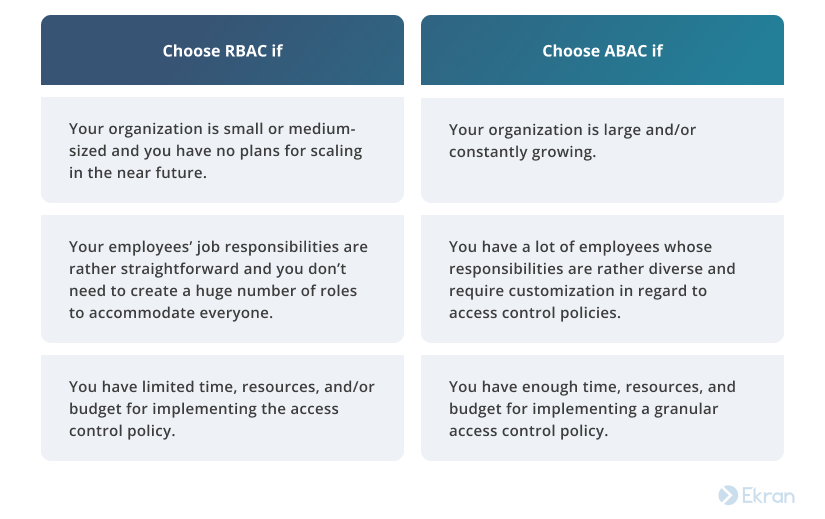
Role-based Access Control (RBAC) vs. Attribute-based Access Control (ABAC) : What's the Difference? | Ping Identity

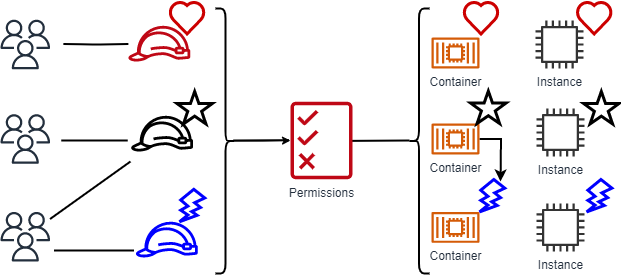
Attribute Based Access Control (ABAC) in a microservices architecture for lists of resources - Stack Overflow

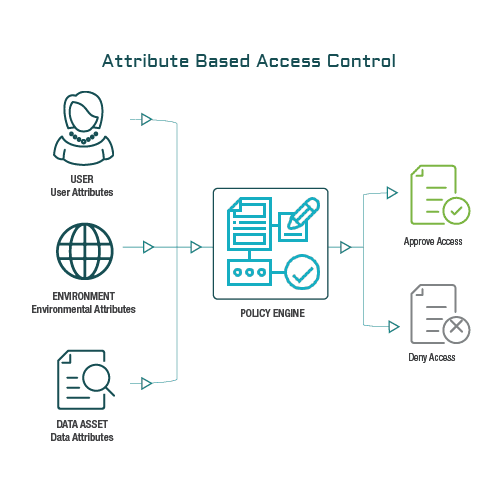
Figure 4 from Guide to Attribute Based Access Control (ABAC) Definition and Considerations | Semantic Scholar